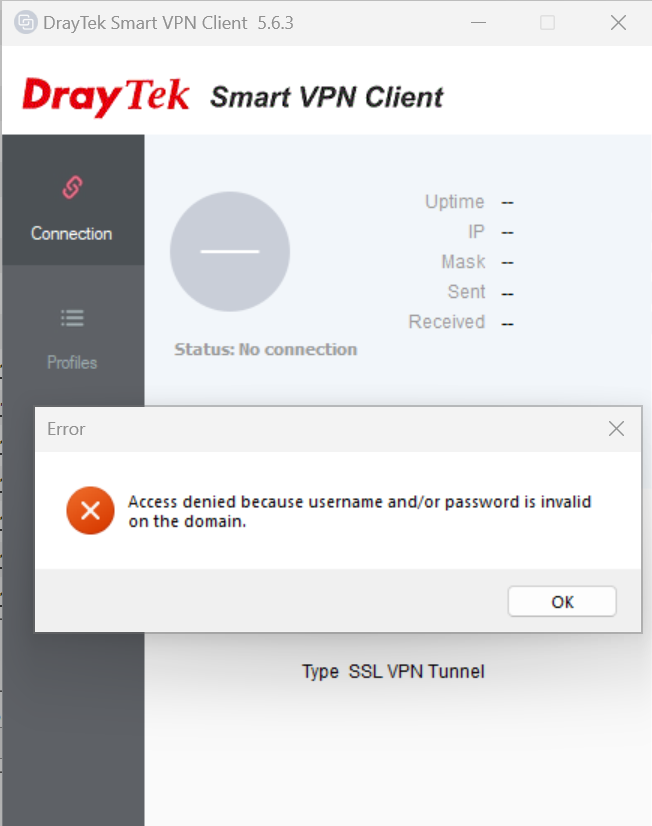
I recently faced a strange issue after configuring and trying to connect to an SSL VPN hosted on a DrayTek Router. I initially updated the DrayTek Smart VPN Client to the latest release 5.6.3 which did not resolve the issue. I then decided to change the SSL VPN Users password and identified that the below error was a result of using the £ symbol in the SSL VPN Users password. Once I removed the £ symbol from the password I was able to connect without error. It’s possible that other special characters may cause the same problem so if you also encounter this error I would initially suggest simplifying your password for testing purposes.
Tag Archives: “vpn client”
Watchguard – SSL VPN clients cannot resolve internal host names despite DNS servers being configured for the connection
You may find that when you configure your Watchguard XTM Firewall to accept SSL VPN connections that clients can connect to
the VPN and ping IP addresses of internal resources, however you cannot resolve internal hosts even via FQDN using DNS. You
may also find that when you run NSLOOKUP on the SSL VPN connected client that the result is your Internet Service Providers
DNS servers rather than the DNS servers assigned via the VPN connection.
To resolve the issue you can change your SSL VPN configuration from a “Routed VPN” to a “Bridge VPN”, the routed VPN uses a
virtual IP address pool (192.168.113.0/24) which does not match your internal IP range or the address range of the internal
DNS Servers. When a Windows client connects to the “Routed VPN” it appears that due to the DNS server mismatch they are not
utilised by the client.
When you configure the VPN in “Bridge VPN” mode you can work around this issue, the Bridge VPN configuration allows you to
exclude some addresses from your Windows DHCP Server Pool and add the into them “Start” and “End” IP addresses on your
Watchguard SSL VPN Configuration Page. The Watchguard will now become responsible for assigning these internal IPs to VPN
clients as they connect rather than the Windows DHCP Server.
You should now find that when your SSL VPN clients connect that they are assigned an IP address and DNS server that are all
within the existing internal IP range of your network. An NSLOOKUP should now return your internal DNS server address and
you should be able to ping hostnames and FQDNs that reside within your internal network.
Examples:
ping windowsserver
ping windowsserver.exampledomain.local
Please remember that the only down side with this configuration is that a “Bridge VPN” bridges to the “Trusted” interface,
this means that the client computer can access any internal resources that they have permissions for by default. A “Routed
VPN” allows you to offer traffic to Optional/secondary networks and gives you more control by letting you lock down access
using “Specify allowed resources”.