HPE iLO
iLO 4
Latest firmware = 2.82
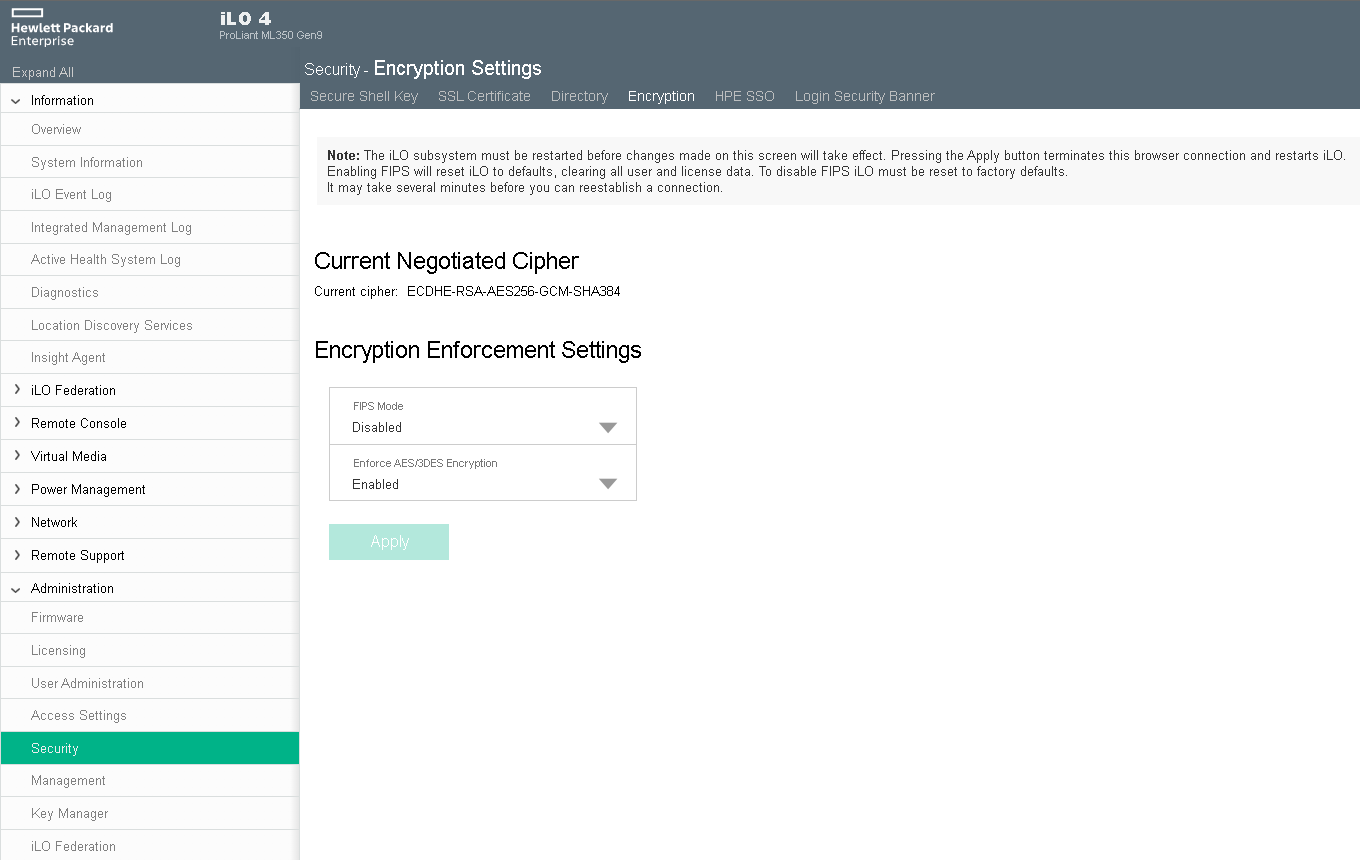
- If you are running iLO4 firmware 2.44 or later then the Enforce AES/3DES Encryption setting only allows TLS 1.2
- If you are running iLO4 firmware 2.50 or later then RC4 was removed from the default cipher list
- If you are running iLO4 firmware 2.50 or later then CBC Mode ciphers are disabled in FIPS/AES Modes
- If you are running iLO4 firmware 2.50 or later then 3DES and SHA-1 are disabled in FIPS mode
- If you are running iLO4 firmware 2.50 or later then the default SSL certificate signing was changed to SHA-256
- If you are running iLO4 firmware 2.81 or later then the weak TLS 1.2 ciphers listed below are disabled in Enforce AES/3DES Encryption mode
- 256-bit AES with RSA, ECDH, and a SHA384 MAC (ECDHE-RSA-AES256-SHA384)
- 256-bit AES with RSA, DH, and a SHA256 MAC (DHE-RSA-AES256-SHA256)
- 128-bit AES with RSA, ECDH, and a SHA256 MAC (ECDHE-RSA-AES128-SHA256)
- 128-bit AES with RSA, DH, and a SHA256 MAC (DHE-RSA-AES128-SHA256)
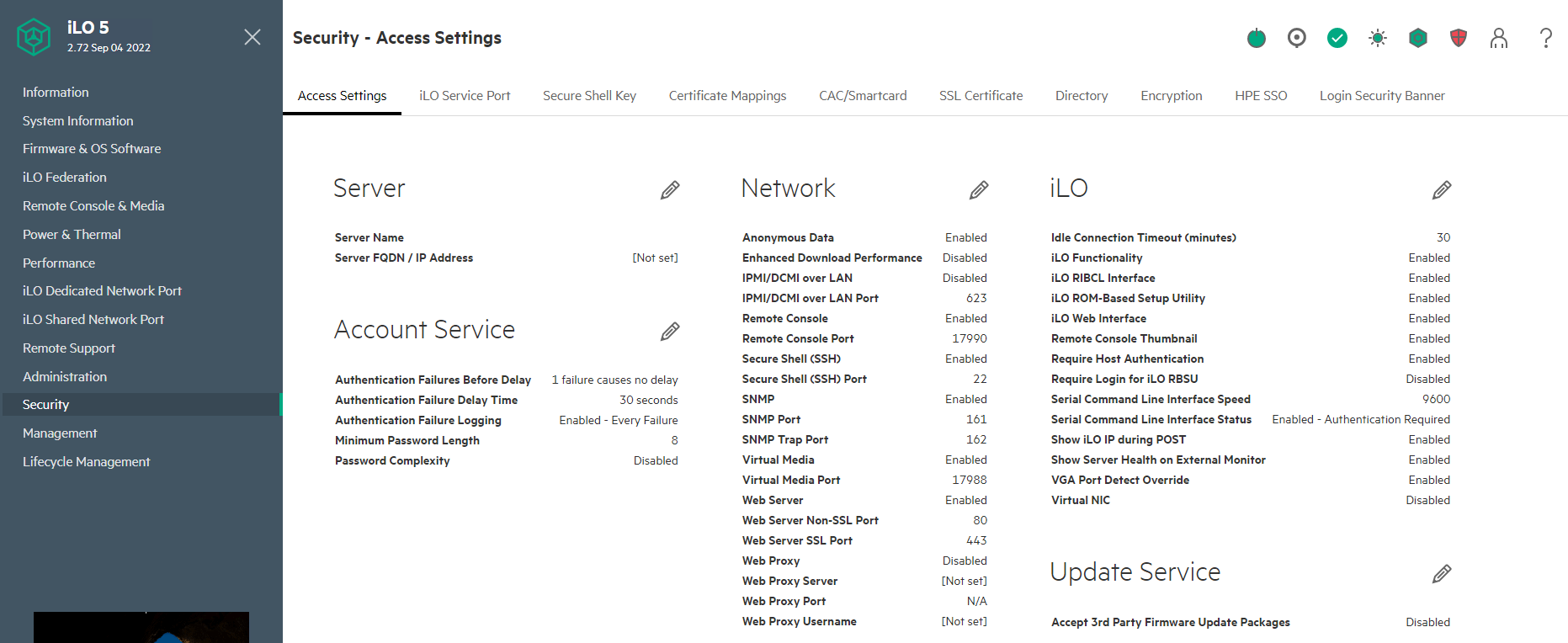
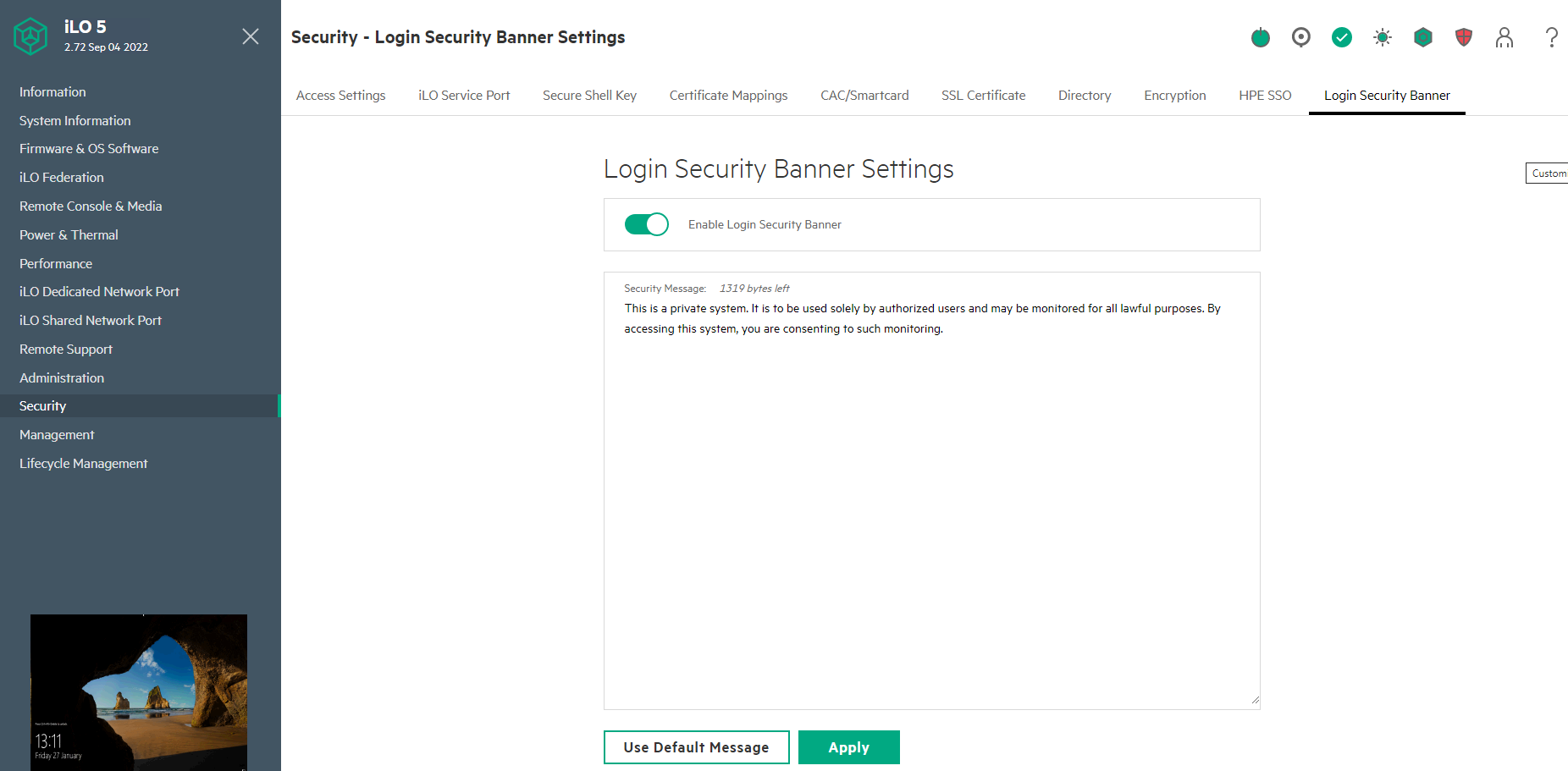
iLO5
Latest firmware = 2.97
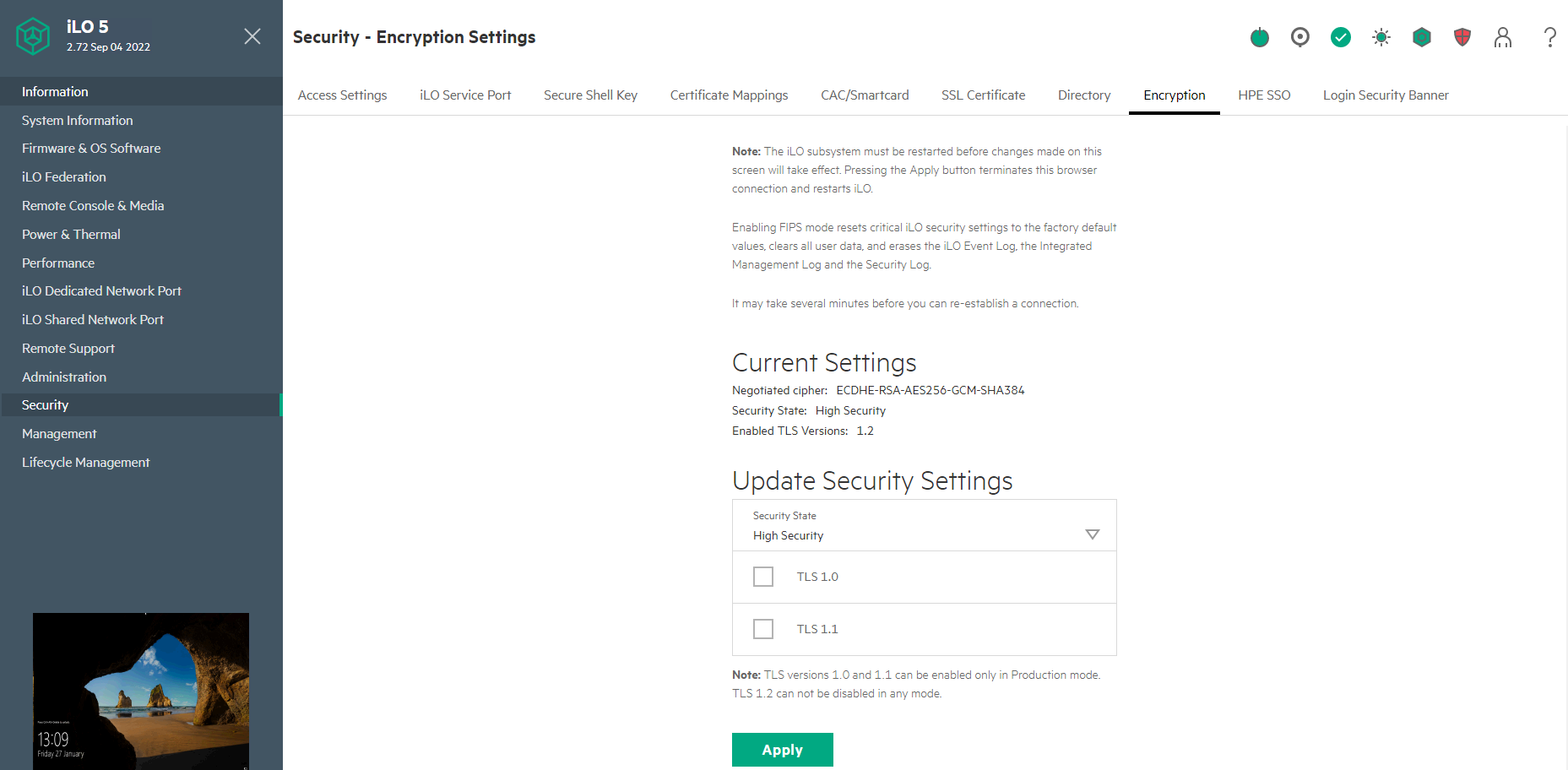
- If you are running iLO5 firmware 2.72 or later then a new option was introduced to disable TLS 1.0 and TLS 1.1
- If you are running iLO5 firmware 2.72 or later then the weak TLS 1.2 ciphers listed below are disabled when in High Security State
- 256-bit AES with RSA, ECDH, and a SHA384 MAC (ECDHE-RSA-AES256-SHA384)
- 256-bit AES with RSA, DH, and a SHA256 MAC (DHE-RSA-AES256-SHA256)
- 128-bit AES with RSA, ECDH, and a SHA256 MAC (ECDHE-RSA-AES128-SHA256)
- 128-bit AES with RSA, DH, and a SHA256 MAC (DHE-RSA-AES128-SHA256
iLO6
Latest firmware = 1.51