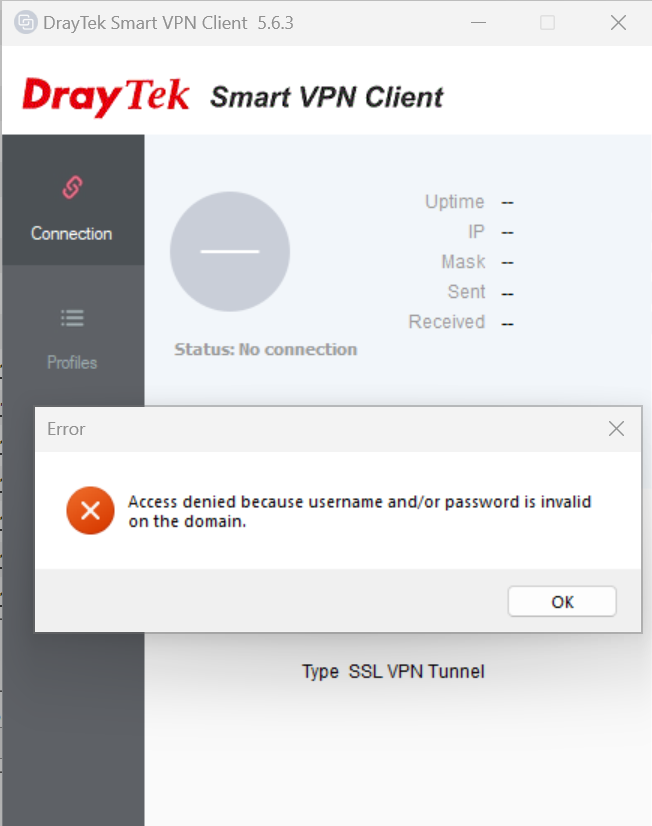
I recently faced a strange issue after configuring and trying to connect to an SSL VPN hosted on a DrayTek Router. I initially updated the DrayTek Smart VPN Client to the latest release 5.6.3 which did not resolve the issue. I then decided to change the SSL VPN Users password and identified that the below error was a result of using the £ symbol in the SSL VPN Users password. Once I removed the £ symbol from the password I was able to connect without error. It’s possible that other special characters may cause the same problem so if you also encounter this error I would initially suggest simplifying your password for testing purposes.
Tag Archives: VPN
How to report Brute Force Attacks
IPinfo allows you to reliably identify important information about an abusive IP including City, Region and Country. It also provides abuse information that will allow you to report the abuse to the netblock owner, you will usually need to provide Firewall and/or event logs that detail the attack. In some instances the attack may have been made from an anonymous VPN service, they are unlikely to have any logs of who undertook the attack but may be able to block your IP address or IP Range from their network.
https://ipinfo.io/
AbuseIPDB allows you to easily check the report history of any IP Address where Brute Force Attacks are originating from, you can also register for free to report abusive IP addresses
https://www.abuseipdb.com/
Watchguard XTM 2 Series, XTM 3 Series, XTM 5 Series, XTM 8 Series – Fireware XTM OS 11.5.3 Build # 339420
Watchguard XTM 2 Series, XTM 3 Series, XTM 5 Series, XTM 8 Series – Fireware XTM OS 11.5.3 Build # 339420
Fireware XTM OS 11.5.3 Build # 339420 Resolves the following issues:
Minor enhancements
• Changes to the routes section of the Firebox System Manager Status Report to improve consistency in the way IPv4 and IPv6 routes are displayed.
• New IP address validity checking in Mobile VPN configurations to help prevent common errors with overlapping IP addresses.
General
• An instability issue found on some XTM 2 devices, where the device could pass traffic normally but could not be managed with WSM or Web UI, has been fixed. [64546]
• A Support Snapshot (a support.tgz file) can now be correctly saved to a USB drive. [64897]
Policy Manager
• You can now use an IP address with a leading zero (10.19.09.0 vs 10.19.9.0) without causing branch office VPN failures. [65189]
• Policy Manager now updates the Mobile VPN with IPSec policies when the configured Virtual IP Address Pool is changed. [65241]
Authentication
• The Event Log Monitor has been enhanced to more effectively retrieve group information in a clientless SSO environment. [65300]
• The SSO Client now responds appropriately when a client computer resumes from a hibernate or sleep state. [65561]
• In the SSO Setup Wizard, the Event Log Monitor check box is now clear by default. [65825]
• The SSO Agent can now correctly load configuration information when the network interface is unavailable. [65802]
Proxies
• HTTP proxy performance has been improved when downloading very large files. [65967]
• A chunking handling issue in the HTTP proxy has been resolved. [65505]
• The SMTP proxy now correctly detects a multi-line 550 response as a valid response. [64463]
• When you use TLS with the default optional allowed rules in the SMTP proxy, email messages can now be delivered successfully to mail servers that do not support TLS. [64650]
• A SIP ALG memory leak issue has been resolved. [65749]
• The SIP ALG now allows provisional ACKs. [65247]
• A problem that caused the SIP ALG to crash has been resolved. [60222]
Security Services
• Gateway AV now detects password-encrypted virus attachments as scan errors. [65047]
• Gateway AV signature update memory utilization has been optimized in this release. This prevents Gateway AV scanning failures caused by a lack of memory. [64940, 64511, 62222]
• The HTTP response no longer stalls when both Gateway AV and RED are enabled. [65877]
• The UTF8 encoded X-WatchGuard-AntiVirus header no longer breaks attachments with long file names. [64883]
• WebBlocker can now correctly fail over to a configured backup server. [65211]
Centralized Management
• Device configuration templates that contain a TCP-UDP proxy policy and a WebBlocker action now work correctly with WatchGuard devices running Fireware XTM v11.3.x. [65408]
Logging & Reporting
• The frequently seen log message: “failed to get routing rules” has been suppressed. [65463]
• A problem that caused log messages to take up to 15 minutes to fail over to a backup Log Server in some networks has been resolved. [62275]
• The Log Collector can now gracefully recover from errors related to a lack of shared memory. [65101]
• Report Manager no longer shows “500 Internal Server Error” when you try to get access to device reports on February 29th of a calendar leap year. [65735]
• Report Manager can now successfully generate PDF output for reports that contain a bar chart. [65099]
• Report Server no longer stops responding to requests while it generates ConnectWise reports data. [65725]
• The Application Usage and Blocked Applications reports no longer display the incorrect IP address value in the y-axis. [65302]
• You can now specify “https://” as part of the ConnectWise Server address without causing WatchGuard Server Center to fail. [64712]
Networking
• Configuration files that include a large number of 1-to-1 NAT entries no longer cause a traffic interruption when saved. [60037]
• A problem that caused a significant memory spike when you configured the DHCP server lease time to one second has been resolved. [65242]
• A problem that caused XTM device performance degradation to occur on devices configured with at least one VLAN interface and many secondary IP addresses has been resolved. [65591]
FireCluster
• A problem that could cause members in a cluster to lock up until rebooted has been resolved. This problem would only occur on a cluster for which proxies were configured. [61091]
• A crash that could occur when one or more connections spanned multiple failovers (at least two failovers in a row) has been corrected. [66008, 66177]
• A problem that could cause connections to time out prematurely has been corrected. In most cases, the symptom would be the disruption of a service (e.g. an FTP download would fail). The problem could affect connections assigned to the non-master of an Active/Active cluster or connections assigned to the new master of an Active/Passive cluster following a failover. [66110]
• Log messages about a FireCluster reboot have been improved to include the reason for the reboot. [65115]
• A problem that prevented a FireCluster failover from occurring because of an error in interpreting the health of the FireCluster Monitored Port has been resolved. [65441]
• An Application Control bug that caused both members of an active/passive FireCluster to reboot has been resolved. [65770]
Mobile VPN with SSL
• Policy Manager and Web UI now display a warning message if Mobile VPN with SSL is enabled and the external IP address of the XTM device is modified. [65806]
• A problem that caused the Mobile VPN with SSL client to crash when connecting from a computer using the Mac OSX 64-bit operating system has been resolved. [65776]
• The Mobile VPN with SSL client running on a computer using Windows 7 64-bit OS can now operate correctly with a third-party web server certificate. [65535]
Mobile VPN with IPSec
• The Mobile VPN with IPSec Shrew Soft client can now connect to an XTM device configured with a static IP address. [64920]
Branch Office VPN
• The latency of packets that traverse a branch office VPN tunnel has been improved. [65333]
• This release resolves a problem that caused an IKEd stacktrace issue in FireCluster. [63108, 65292]
CLI
• You can now use the CLI vlan-id command with the “external dhcp” option successfully. [65478]
• The CLI show sysinfo command now displays the correct CPU utilization values. [64521]
You can download Fireware XTM OS 11.5.3 Build # 339420 from the Watchguard website.
Please note that Watchguard XTM OS releases are cumulative so you should only need to apply the latest OS to ensure that you also have any previous fixes/features.
[RESOLVED] Google Android ICS 4.0, 4.01 or 4.02 – Handset Crashes and Reboots when you try to connect to an IPSec Xauth PSK VPN over the 3G Mobile Network
You may find that your Google Android ICS 4.0, 4.01 or 4.02 Smart Phone crashes and reboots when you try to connect to an IPSec Xauth PSK VPN over the 3G Mobile Network. This has been seen to occur with Watchguard and Cisco VPN connections and is related to a glitch in the Google Android Modem Driver.
You will need to wait for an Over the Air update to Google Android 4.0.3 for the issue to be resolved, if this issue is severely affecting you then you may be able to contact your moile network carrier and/or the handset manufacturer to arrange to have the phone updated earlier.
Further information about this issue can be found here: http://code.google.com/p/android/issues/detail?id=23404&can=1&q=vpn%20xauth&colspec=ID Type Status Owner Summary Stars