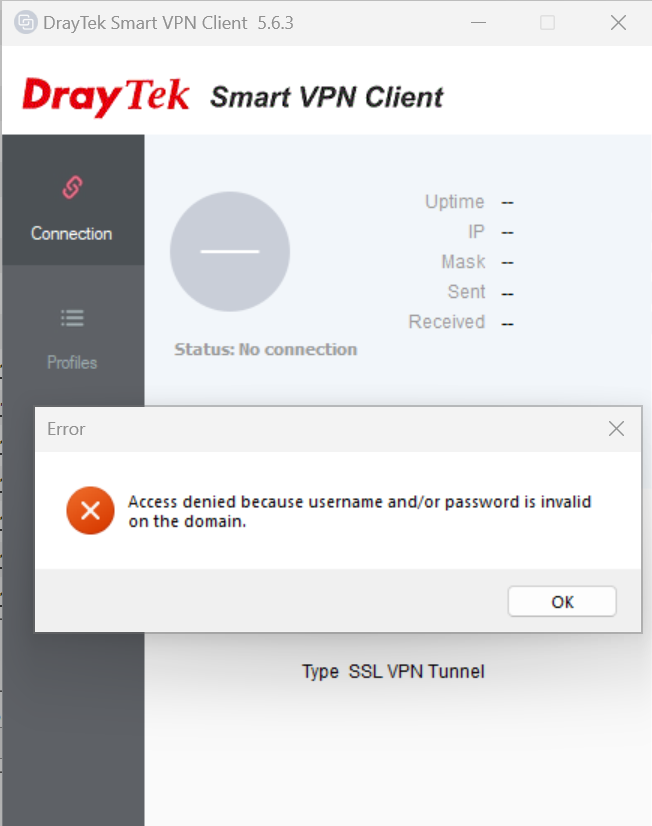
I recently faced a strange issue after configuring and trying to connect to an SSL VPN hosted on a DrayTek Router. I initially updated the DrayTek Smart VPN Client to the latest release 5.6.3 which did not resolve the issue. I then decided to change the SSL VPN Users password and identified that the below error was a result of using the £ symbol in the SSL VPN Users password. Once I removed the £ symbol from the password I was able to connect without error. It’s possible that other special characters may cause the same problem so if you also encounter this error I would initially suggest simplifying your password for testing purposes.
This list includes some of the FQDNs and IP Addresses used by Sophos Services, this may be useful for identifying outgoing traffic and creating web filtering exceptions.
*.cloudfront.net
*.ctr.sophos.com
*.hydra.sophos.com
*.sophos.com
*.sophosupd.com
*.sophosupd.net
*.sophosxl.net
108.128.21.191
108.128.75.57
176.34.202.39
18.200.140.39
18.200.233.166
18.200.76.187
18.201.4.220
23.56.184.93
3.248.161.254
3.248.236.19
3.248.239.225
34.240.132.250
34.240.132.63
34.240.70.198
34.240.87.136
34.241.47.153
34.242.175.229
34.242.189.0
34.242.190.168
34.243.109.72
34.243.155.26
34.243.46.159
34.246.1.161
34.246.93.20
34.247.133.51
34.247.19.150
34.248.0.181
34.249.116.122
34.249.16.38
34.249.213.108
34.249.56.234
34.249.75.71
34.250.177.130
34.250.201.204
34.250.232.147
34.251.0.214
34.251.206.176
34.252.99.77
34.253.34.19
34.254.24.5
4.sophosxl.net
46.137.119.69
46.51.205.49
52.16.156.95
52.16.224.248
52.18.132.38
52.18.142.239
52.18.201.121
52.19.111.54
52.19.130.35
52.19.133.193
52.208.138.248
52.208.151.187
52.208.47.80
52.208.61.137
52.209.113.230
52.209.174.16
52.209.74.179
52.211.118.19
52.211.181.255
52.211.215.132
52.211.33.11
52.211.40.77
52.212.179.152
52.212.19.181
52.212.243.39
52.212.80.79
52.213.185.15
52.213.222.108
52.213.224.21
52.213.227.181
52.213.81.142
52.214.122.237
52.214.193.2
52.215.191.67
52.31.157.236
52.48.158.77
52.48.251.68
52.49.52.52
52.49.55.251
52.51.136.43
52.51.19.238
54.154.78.113
54.155.110.171
54.155.150.168
54.155.54.127
54.171.179.249
54.171.2.113
54.171.211.242
54.171.39.210
54.171.82.87
54.194.136.103
54.194.149.107
54.194.158.193
54.194.23.13
54.194.31.233
54.216.250.187
54.220.121.131
54.228.154.173
54.229.182.239
54.229.193.103
54.229.26.205
54.229.29.253
54.246.206.153
54.246.225.42
54.73.159.85
54.73.59.214
54.75.131.11
54.76.53.13
54.77.101.166
54.77.103.108
54.77.109.237
54.77.183.40
54.77.190.39
54.78.168.73
54.78.85.182
63.32.154.88
63.32.247.92
63.34.49.237
63.35.134.40
99.81.41.145
99.81.95.11
amazonaws.com
api.stn100yul.ctr.sophos.com
api-cloudstation-us-east-2.prod.hydra.sophos.com
az416426.vo.msecnd.net
central.sophos.com
cloud.sophos.com
cloud-assets.sophos.com
d1.sophosupd.com
d1.sophosupd.net
d2.sophosupd.com
d2.sophosupd.net
d3.sophosupd.com
d3.sophosupd.net
dc.services.visualstudio.com
dci.sophosupd.com
dci.sophosupd.net
downloads.sophos.com
dzr-api-amzn-eu-west-1-9af7.api-upe.p.hmr.sophos.com
dzr-mcs-amzn-eu-west-1-9af7.upe.p.hmr.sophos.com
dzr-mcs-amzn-us-west-2-fa88.upe.p.hmr.sophos.com
http.00.a.sophosxl.net
http.00.s.sophosxl.net
id.sophos.com
mcs.stn100hnd.ctr.sophos.com
mcs.stn100syd.ctr.sophos.com
mcs.stn100yul.ctr.sophos.com
mcs2.stn100hnd.ctr.sophos.com
mcs2.stn100syd.ctr.sophos.com
mcs2.stn100yul.ctr.sophos.com
mcs2-cloudstation-eu-central-1.prod.hydra.sophos.com
mcs2-cloudstation-eu-west-1.prod.hydra.sophos.com
mcs2-cloudstation-us-east-2.prod.hydra.sophos.com
mcs2-cloudstation-us-west-2.prod.hydra.sophos.com
mcs-cloudstation-eu-central-1.prod.hydra.sophos.com
mcs-cloudstation-eu-west-1.prod.hydra.sophos.com
mcs-cloudstation-us-east-2.prod.hydra.sophos.com
mcs-cloudstation-us-west-2.prod.hydra.sophos.com
samples.sophosxl.net
sdds3.sophosupd.com
sdds3.sophosupd.net
sdu-feedback.sophos.com
sophos.com
sophosupd.com
sophosxl.net
ssp.feedback.sophos.com
sus.sophosupd.com
sus.sophosupd.net
t1.sophosupd.com
HPE iLO
iLO 4
Latest firmware = 2.82
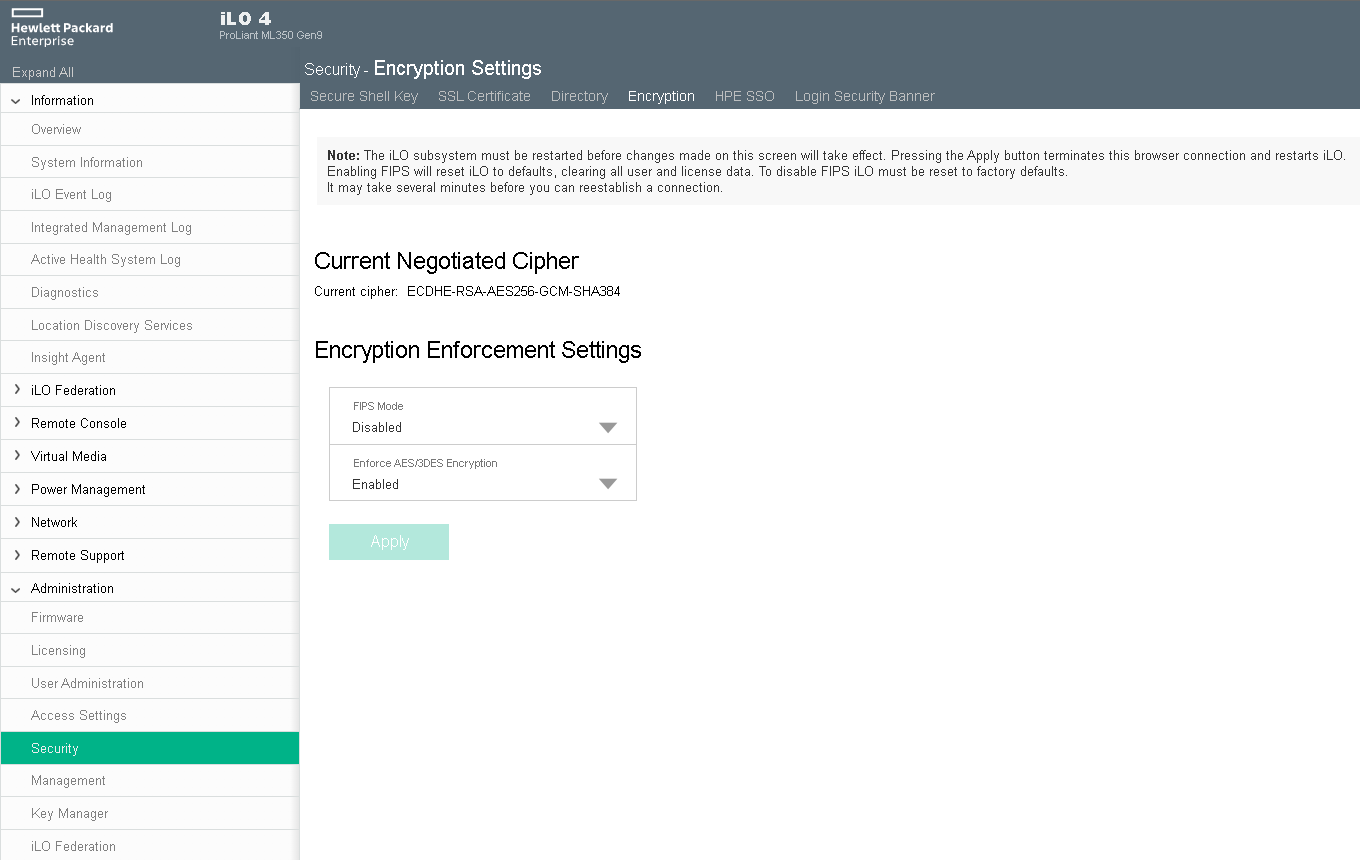
If you are running iLO4 firmware 2.44 or later then the Enforce AES/3DES Encryption setting only allows TLS 1.2
If you are running iLO4 firmware 2.50 or later then RC4 was removed from the default cipher list
If you are running iLO4 firmware 2.50 or later then CBC Mode ciphers are disabled in FIPS/AES Modes
If you are running iLO4 firmware 2.50 or later then 3DES and SHA-1 are disabled in FIPS mode
If you are running iLO4 firmware 2.50 or later then the default SSL certificate signing was changed to SHA-256
If you are running iLO4 firmware 2.81 or later then the weak TLS 1.2 ciphers listed below are disabled in Enforce AES/3DES Encryption mode
256-bit AES with RSA, ECDH, and a SHA384 MAC (ECDHE-RSA-AES256-SHA384)
256-bit AES with RSA, DH, and a SHA256 MAC (DHE-RSA-AES256-SHA256)
128-bit AES with RSA, ECDH, and a SHA256 MAC (ECDHE-RSA-AES128-SHA256)
128-bit AES with RSA, DH, and a SHA256 MAC (DHE-RSA-AES128-SHA256)
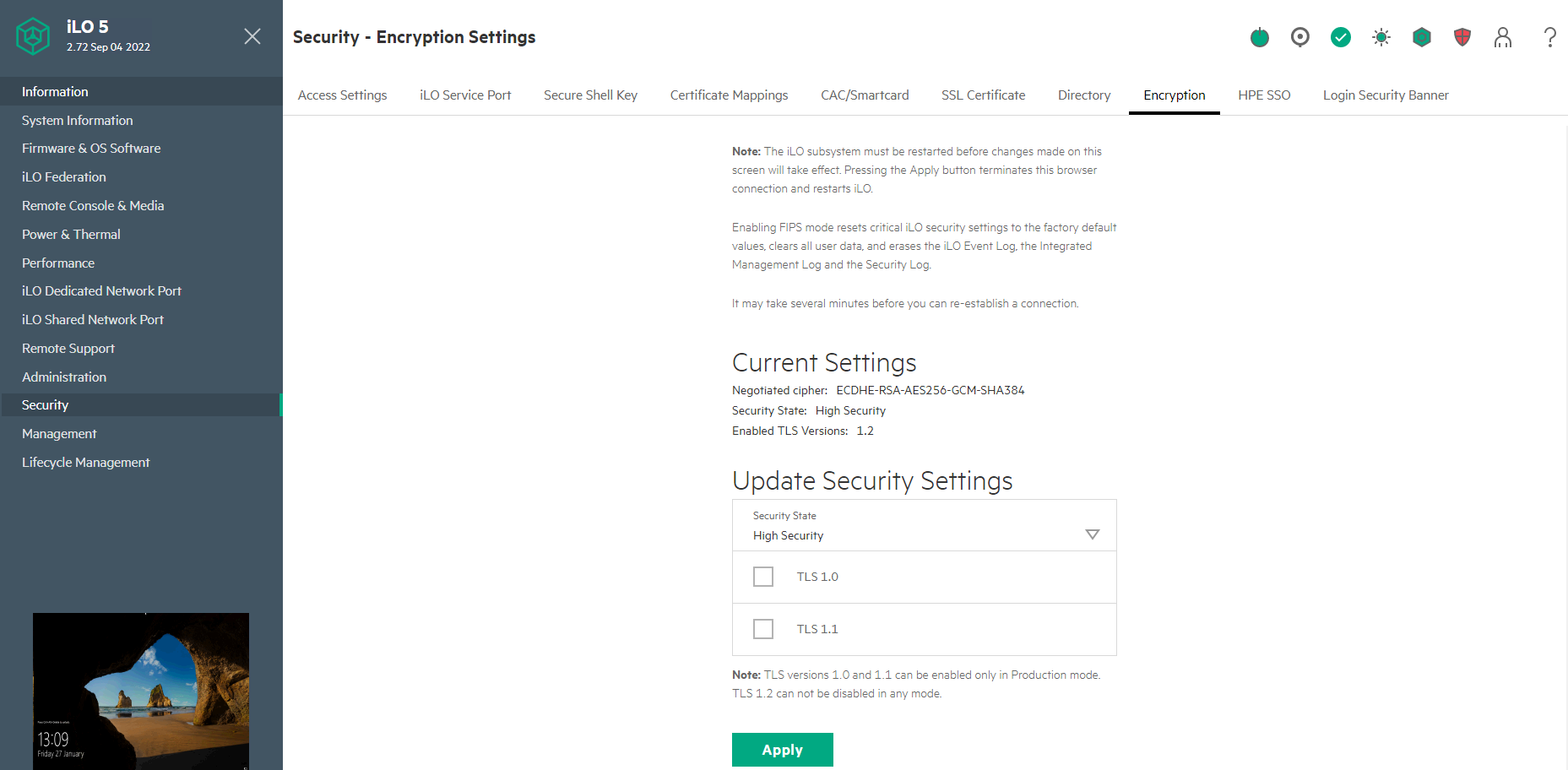
iLO5
Latest firmware = 2.97
If you are running iLO5 firmware 2.72 or later then a new option was introduced to disable TLS 1.0 and TLS 1.1
If you are running iLO5 firmware 2.72 or later then the weak TLS 1.2 ciphers listed below are disabled when in High Security State
256-bit AES with RSA, ECDH, and a SHA384 MAC (ECDHE-RSA-AES256-SHA384)
256-bit AES with RSA, DH, and a SHA256 MAC (DHE-RSA-AES256-SHA256)
128-bit AES with RSA, ECDH, and a SHA256 MAC (ECDHE-RSA-AES128-SHA256)
128-bit AES with RSA, DH, and a SHA256 MAC (DHE-RSA-AES128-SHA256
iLO6
Latest firmware = 1.51
Iiscore.dll – Pre Service Pack 1 Revision History for Windows 8 RTM and Windows Server 2012 RTM
10-Oct-2012 – 8.0.9200.20533 – Iiscore.dll – x86/x64 – http://support.microsoft.com/kb/2763973 – FIX: “HTTP 403 (Forbidden)” when a client HTTPS request is sent to a Web application or a Web service in IIS 7.5 or IIS 8.0 and uses a self-signed certificate
10-Oct-2012 – 8.0.9200.16432 – Iiscore.dll – x86/x64 – http://support.microsoft.com/kb/2763973 – FIX: “HTTP 403 (Forbidden)” when a client HTTPS request is sent to a Web application or a Web service in IIS 7.5 or IIS 8.0 and uses a self-signed certificate
Posts navigation
IT – Software and Hardware Support Resources