Lets start by taking a look under “c:\Users” if you find multiple TEMP.DOMAINNAME.XXX folders then read on.
You may see the following two events logged together in the Application Event Log on the SBS 2011 Server and both reference the DOMAINNAME\spwebapp
Log Name: Application
Source: User Profile Service
Event ID: 1500
Lvel: Error
Windows cannot log you on because your profile cannot be loaded. Check that you are connected to the network, and that your network is functioning correctly.
DETAIL – The system cannot find the file specified.
and
Log Name: Application
Source: User Profile Service
Event ID: 1501
Lvel: Error
Windows cannot create a temporary profile directory. This problem may be caused by insufficient security rights.
DETAIL – The system cannot find the file specified.
You may also see the following event logged in the System Event Log on the SBS 2011 Server
Log Name: System
Source: WAS
Event ID: 5022
Lvel: Warning
The Windows Process Activation Service failed to create a worker process for the application pool ‘SBS Sharepoint AppPool’. The data field contains the error number.
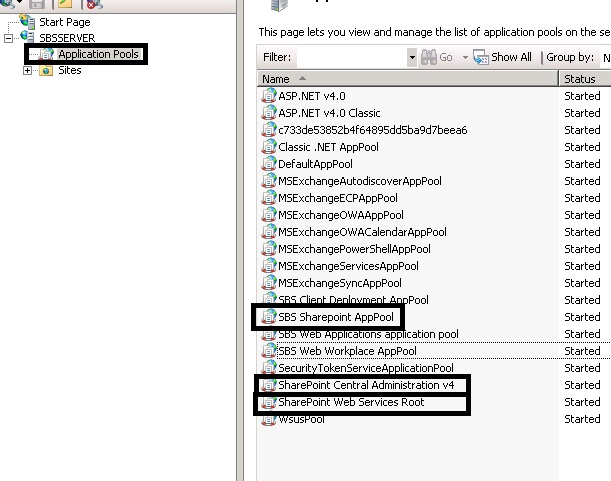
If you are seeing the above errors then you need to cut and paste all the TEMP.DOMAINNAME.XXX folders from “c:\Users” into a “new folder” on your desktop for example (you should not need these temp profiles again but it’s best to keep them to one side). Once you no longer have any of these folders in the “C:\users” directory we need to launch “Internet Information Services (IIS) Manager” from Administrative Tools and then expand the server and click on “Application Pools”. Once in “Application Pools” you need to stop the three highlighted Pools “SBS Sharepoint AppPool”, “SharePoint Central Administration v4” and “SharePoint Web Services Root”. Once all three are stopped wait about 10-20 seconds and then start these three stopped Pools.
 Now that you have followed all these steps launch your web browser and try to navigate to http://companyweb and your SharePoint site should load correctly. Please note that the Companyweb SharePoint site might take 20-30 seconds to load the first time whilst the profile is re-created, after this it should be nice and fast.
Now that you have followed all these steps launch your web browser and try to navigate to http://companyweb and your SharePoint site should load correctly. Please note that the Companyweb SharePoint site might take 20-30 seconds to load the first time whilst the profile is re-created, after this it should be nice and fast.